Cbrutekrag is penetration tests on SSH servers using dictionary attacks. Written in C. А powerful tool for penetration tests on SSH servers using dictionary attacks. Written in C, this tool allows security analysts to simulate real-world attacks and assess the strength of their systems against brute-force attempts. With its advanced algorithms and extensive wordlist support, Cbrutekrag can quickly crack even the most complex passwords.
One of the key advantages of using Cbrutekrag is its versatility. This tool can be used on any SSH server, regardless of the operating system or configuration. Furthermore, it supports both single-threaded and multi-threaded modes, allowing users to optimize their testing based on their hardware resources. Additionally, provides detailed statistics on each attack attempt, making it easy to identify successful breaches and areas for improvement.
brute krag means “brute force” in afrikáans
Disclaimer
This tool is for ethical testing purpose only.
cbrutekrag and its owners can’t be held responsible for misuse by users.
Users have to act as permitted by local law rules.
Requirements
uses libssh – The SSH Library (http://www.libssh.org/)
The SSH Library is a free and open-source C library that implements the SSH protocol. The library allows developers to incorporate secure communication in their applications without having to worry about the underlying cryptographic details. It provides a simple API for creating client and server applications using SSH.
With its modern architecture, the libssh library supports all major SSH protocol versions, including 1.5, 1.99, and 2.0. It also provides support for various authentication methods such as password-based authentication, public key authentication, keyboard-interactive authentication, and GSSAPI-based authentication.
The libssh library offers several features that make it an excellent choice for implementing secure communication in applications. For instance, it supports channel multiplexing which allows multiple channels over a single connection; this feature helps reduce latency by avoiding the overhead of opening new connections for each request/response cycle.
Build
Requirements:
makegcccompilerlibssh-dev
git clone --depth=1 https://github.com/matricali/cbrutekrag.git
cd cbrutekrag
make
make installStatic build
Requirements:
cmakegcccompilermakelibssl-devlibz-dev
git clone --depth=1 https://github.com/matricali/cbrutekrag.git
cd cbrutekrag
bash static-build.sh
make installRun
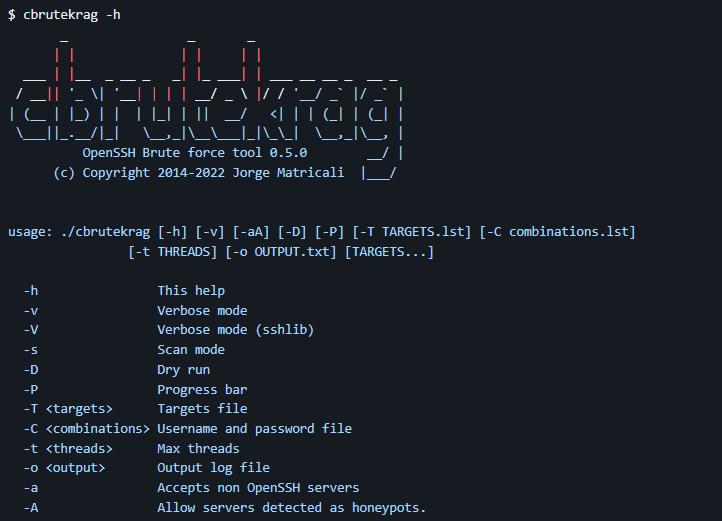
$ cbrutekrag -h
_ _ _
| | | | | |
___ | |__ _ __ _ _| |_ ___| | ___ __ __ _ __ _
/ __|| '_ \| '__| | | | __/ _ \ |/ / '__/ _` |/ _` |
| (__ | |_) | | | |_| | || __/ <| | | (_| | (_| |
\___||_.__/|_| \__,_|\__\___|_|\_\_| \__,_|\__, |
OpenSSH Brute force tool 0.5.0 __/ |
(c) Copyright 2014-2022 Jorge Matricali |___/
usage: ./cbrutekrag [-h] [-v] [-aA] [-D] [-P] [-T TARGETS.lst] [-C combinations.lst]
[-t THREADS] [-o OUTPUT.txt] [TARGETS...]
-h This help
-v Verbose mode
-V Verbose mode (sshlib)
-s Scan mode
-D Dry run
-P Progress bar
-T <targets> Targets file
-C <combinations> Username and password file
-t <threads> Max threads
-o <output> Output log file
-a Accepts non OpenSSH servers
-A Allow servers detected as honeypots.Example usages
cbrutekrag -T targets.txt -C combinations.txt -o result.log
cbrutekrag -s -t 8 -C combinations.txt -o result.log 192.168.1.0/24Supported targets syntax
- 192.168.0.1
- 10.0.0.0/8
- 192.168.100.0/24:2222
- 127.0.0.1:2222
Combinations file format
root root
root password
root $BLANKPASS$