IT Security
IT security and technology has become an integral part of our lives, and the security of IT systems is a major concern for businesses and individuals alike. As threats to cyber security continue to evolve, it is essential to identify hidden risks that can be easily overlooked. In this article, we will explore how IT professionals can identify potential risks and vulnerabilities in their networks.
Common Threats
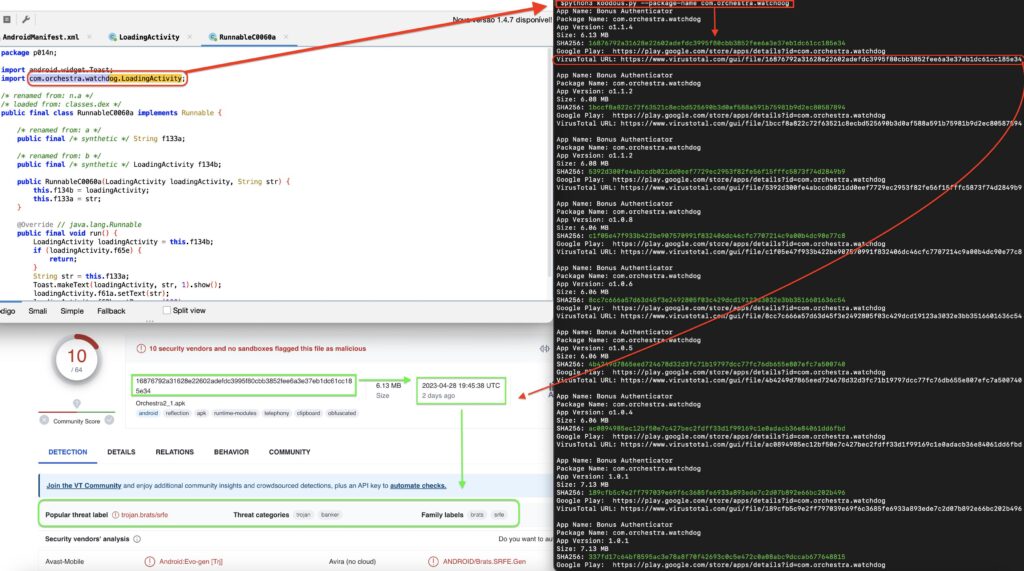
One of the most common threats to is phishing. This involves a fraudulent attempt to obtain sensitive information such as passwords and credit card details through disguised electronic communication. Phishing attacks are usually carried out via email or instant messaging, where the attacker poses as a trustworthy source such as a bank or social media platform. To counteract this threat, it’s important to educate users on how to identify suspicious emails and messages.
Another major threat is malware, which refers to any malicious software that can harm computer systems or networks. Malware can be spread in various ways including email attachments, infected websites, and downloaded files. Once installed, malware can cause significant damage by stealing data, corrupting files, and even taking control of an entire network. To prevent malware from infecting your system it’s essential to use antivirus software and keep all applications up-to-date with the latest security patches.
Lastly, ransomware is becoming increasingly popular among cybercriminals who encrypt your files until you pay a ransom fee. Ransomware typically spreads through malicious downloads or email attachments containing infected links. It’s critical to have backups of all important files stored offsite in case of such an attack so that vital data isn’t lost if you are unable (or unwilling) to pay the ransom fee demanded by attackers.
Data Protection
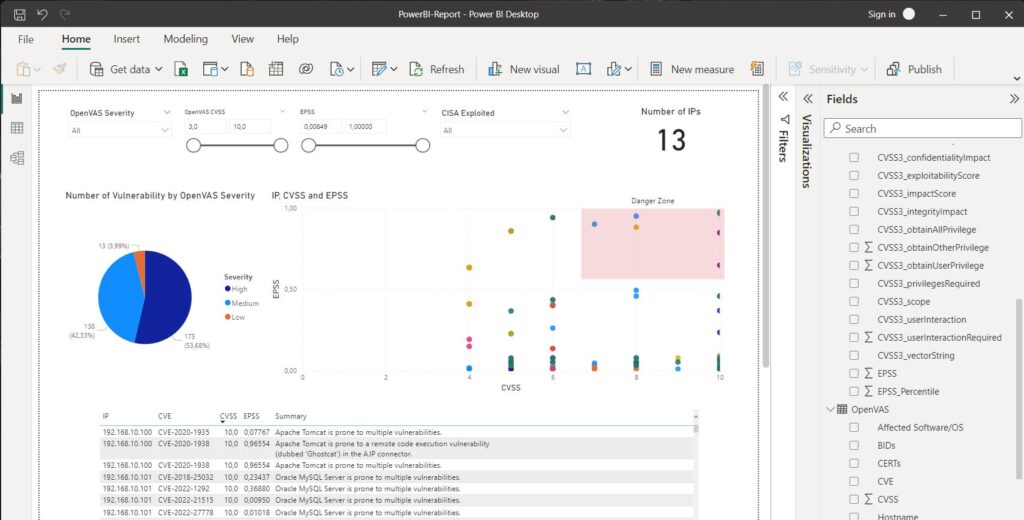
Data protection is a crucial aspect is to ensures the confidentiality, integrity, and availability of data. It involves safeguarding sensitive information from unauthorized access, use, disclosure, modification or destruction. Data breaches can lead to enormous financial losses and damage to an organization’s reputation.
To ensure effective data protection measures are implemented, organizations need to adopt a holistic approach that includes technical controls such as encryption and access control systems. Additionally, employees must be trained on how to handle sensitive information and understand their role in protecting it.
Moreover, compliance with relevant regulations and standards such as GDPR (General Data Protection Regulation) is essential for organizations processing personal data of individuals within the EU region. Failure to comply with these regulations could result in hefty fines imposed by regulatory bodies. In conclusion, implementing robust data protection measures is critical for ensuring the security of organizational assets and maintaining stakeholder trust.
Network Security
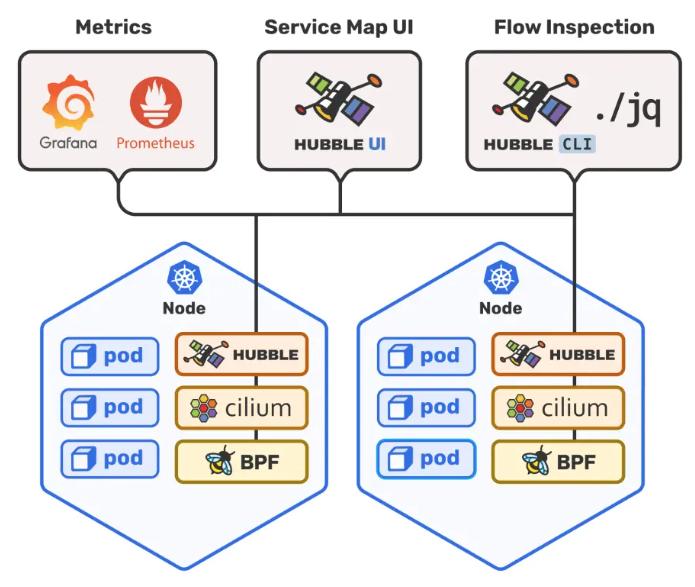
Network security is an essential aspect of IT security. It involves the protection of computer networks from unauthorized access, theft, and destruction. Network security measures include firewalls, intrusion detection systems (IDS), virtual private networks (VPNs), and other security protocols that prevent hackers from accessing sensitive information.
One of the most critical elements in network security is encryption. Encryption ensures that data transmitted over a network cannot be intercepted or read by unauthorized individuals. It involves converting plain text into an unreadable format using mathematical algorithms. Encrypted data can only be decoded with a secret key that is known only to the intended recipient.
Another important aspect of network security is user access management. This involves limiting access to sensitive information to authorized personnel only. User authentication protocols such as passwords, biometrics, and smart cards are used to verify users’ identities before granting them access to the system. By implementing these measures, organizations can protect their networks from insider threats and prevent breaches caused by human error or negligence.